Requests
About Secure Requests
Requests offer a secure way to receive sensitive data, such as text or files, from colleagues, clients, or customers.
This feature allows you to send a request using a secret URL and securely receive a response without compromising security or exposing sensitive data.
Further, to minimize risk and respect recipient data, sensitive information is automatically deleted after a preset duration that you specify.
How Does It Work?
- Create a request.
- A secret URL is generated.
- Share the secret URL with your recipient.
- The recipient responds to the request with text or files.
- Receive a notification when the response is submitted, with a preset time limit for retrieval.
Key Benefits
- Enhanced Security: Requests ensure sensitive data is securely transmitted, managed and deleted, reducing the risk of unauthorized access.
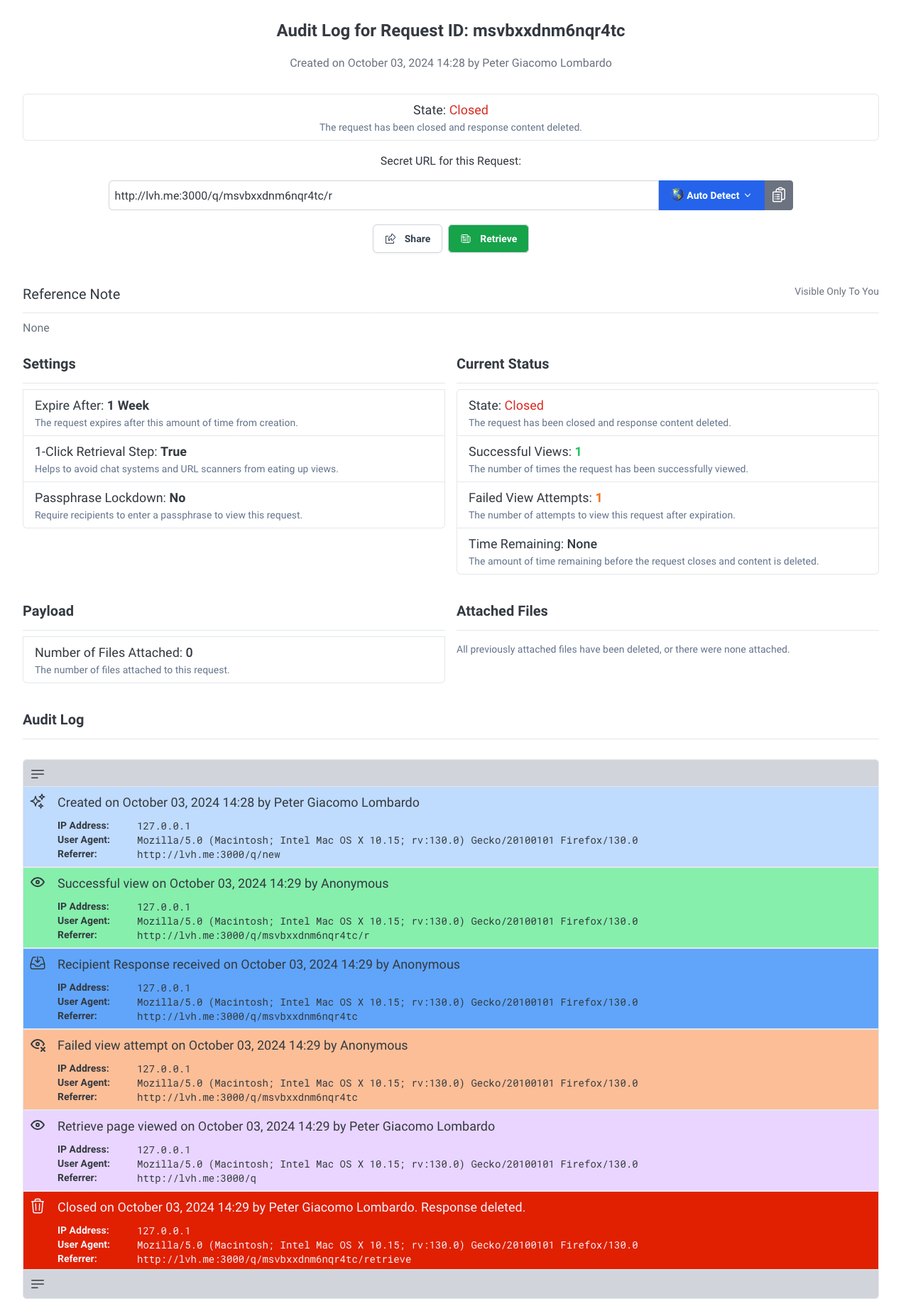
- Lifecycle Audit Logs: Track every stage of the request, including creation, access, response and deletion. Logs show failed access and unauthorized attempts, and are available indefinitely.
- Automatic Deletion: Once a response is received, requests expire and self-delete after a preset duration, ensuring transmitted data is irretrievable after expiration and request closure.
- Compliance: Requests help meet regulatory standards (e.g., GDPR, HIPAA, PCI-DSS) by minimizing the risk of data exposure.
- Improved User Experience: Provides a smooth, secure way to request sensitive data, avoiding the risks of insecure channels.
- Reduced Risk of Data Breaches: Data encryption and secure transmission minimize the impact of potential breaches.
Automatic Expiration and Deletion
Responses to requests automatically expire and self-delete after a preset duration, ensuring recipient data is secure. Set the expiration time when creating a request, and be sure to retrieve the response before the deadline.
Comprehensive Lifecycle Tracking
A detailed audit log tracks every stage of the request’s lifecycle:
- Timestamps: Records creation, access (both successful and failed), expiration, and deletion.
- Access Details: Logs IP addresses, browser signatures, and device information of anyone accessing the request.
- Request Metadata: Includes transmitted data types, expiration status, and deletion confirmation, ensuring complete removal from the system.
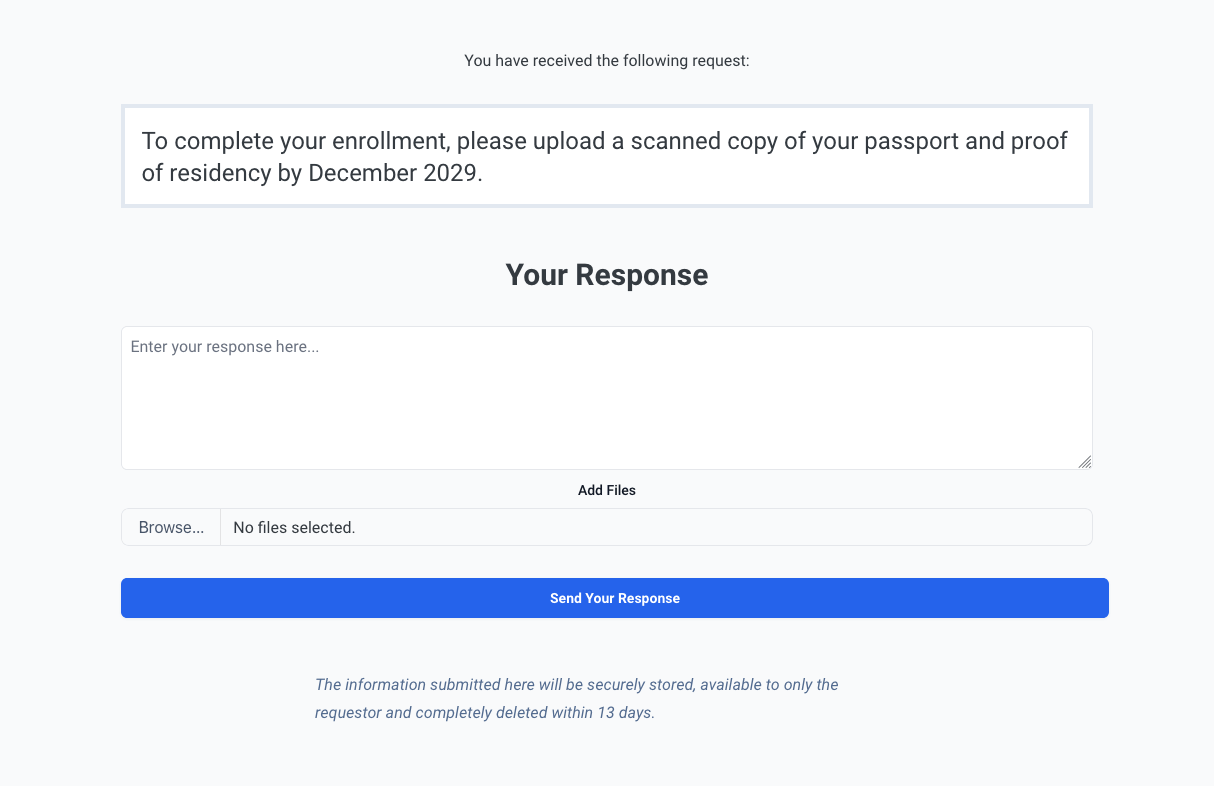
What Do End Users See?
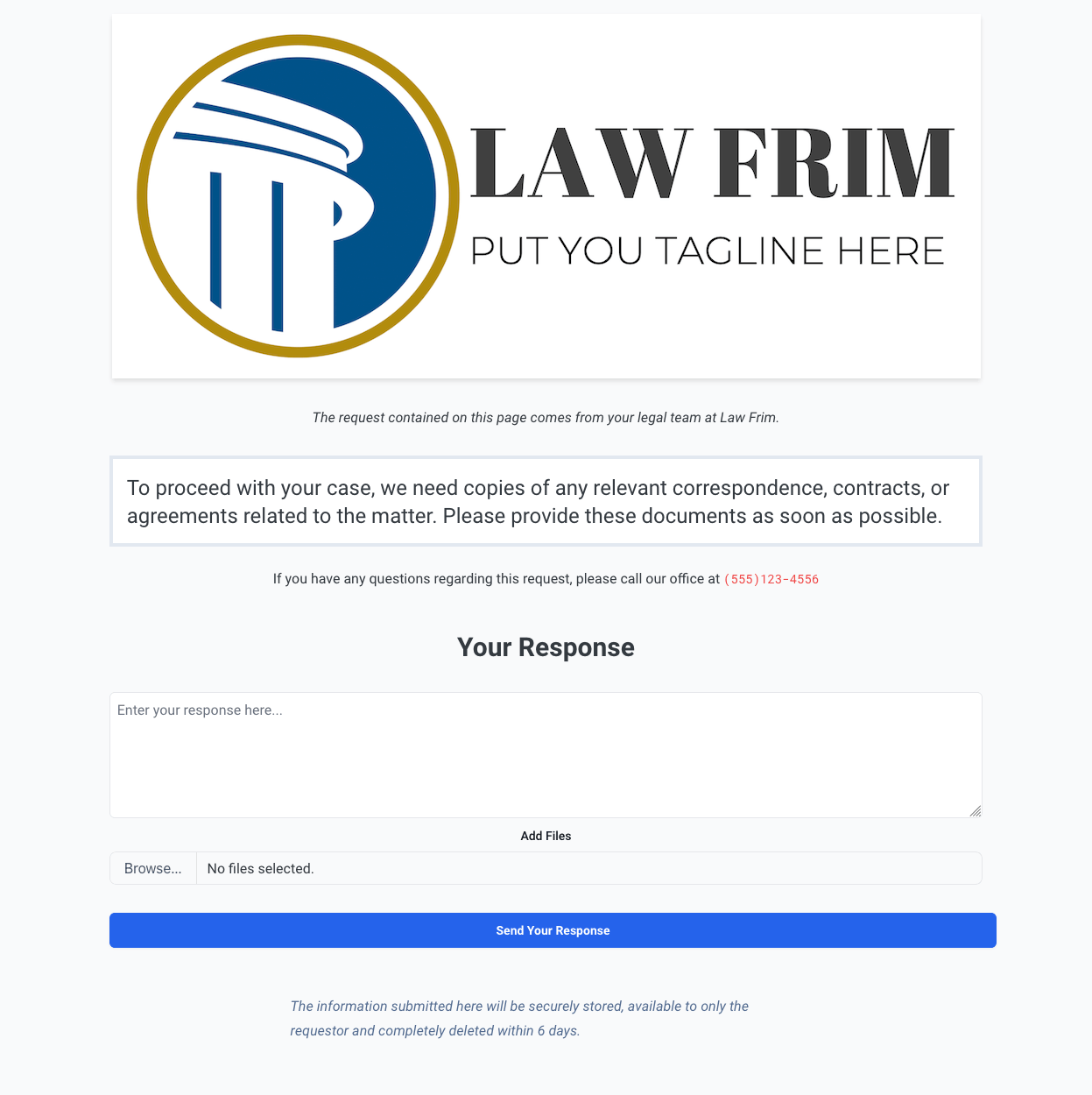
Recipients accessing the secret URL will see a simple, unbranded page displaying the request contents. This streamlined design reduces confusion and enhances the user experience.
Note: Premium & Pro users can utilize branded request pages. Learn more.


Best Practices for Using Requests
- Shorter Expiration Windows: Set shorter expiration times to minimize the risk of exposure.
- Compartmentalize: Don’t request correlated sensitive information like usernames and passwords together; use separate requests.
- Monitor Access & Expiration: Ensure recipients respond promptly, and requests expire quickly.
- Use Passphrase Lockdown: Enable passphrase protection for additional security. Both successful and failed attempts are logged.
