Pushes: Files, Text, URLs & QR Codes
About Pushes: Files, Text, URLs & QR Codes
Pushes are a secure way to transmit sensitive data, such as text, files, or URLs to end users. This feature allows you to send confidential information to users without compromising their security or exposing sensitive data in logs, email, or chat.
Pushes are often used for employee on-boarding, sending new account credentials, transmitting secure files and more.
Why are Pushes Needed?
Traditional methods of transmitting sensitive data, such as email or chat, can pose significant security risks. Logs, email, and chat platforms are vulnerable to unauthorized access, and sensitive information can exist forever and be exposed to unauthorized parties. Pushes provide an additional layer of security by encrypting and securely transmitting sensitive data to end users.
Pushes automatically expire and self-delete.
How do they work?
Here’s a break of the lifecycle of a push:
-
Sender Creates a Push: The sender uses Password Pusher to generate a push. They can customize the number of allowed views, the duration the push will be valid, and optionally set a passphrase for extra security.
-
A Secret URL is Generated: Once the push is created, a unique secret URL is generated for it. This is the link the recipient will use to access the secure information. A secret URL may look like:
https://pwpush.com/p/fjah-38fj2lanvbfke. -
Sender Shares the URL: The sender shares the secret URL with the recipient.
-
Recipient Views the Push: The recipient clicks the secret URL to view the protected information. Each time the URL is accessed, it is logged in an audit trail.
-
Limited Views and Expiration: The push can only be viewed as many times as the sender allowed. Once the allowed views or the set expiration time is reached, the push expires, and all sensitive information is permanently deleted.
-
Audit Log: Even after the push expires, the sender can access the audit log from their dashboard to see when and how the push was accessed for record-keeping purposes.
Benefits of Pushes
- Enhanced Security: pushes ensure that sensitive data is transmitted securely, reducing the risk of unauthorized access or exposure.
- Observable Lifecycle: pushes include an comprehensive Audit Log that tracks the entire lifecycle of a push from creation to expiration and deletion. Audit Logs are available indefinitely and also show failed access and unauthorized access attempts.
- Automatic Deletion: Pushes automatically expire and self-delete after a preset duration of number of views. Transmitted information is irretrievable after push expiration.
- Compliance: pushes help organizations comply with regulatory requirements, such as GDPR, HIPAA, and PCI-DSS, by minimizing the risk of sensitive data exposure.
- Improved User Experience: pushes provide a seamless and secure way to transmit sensitive data, reducing the need for users to share sensitive information through insecure channels.
- Reduced Risk of Data Breaches: By encrypting and securely transmitting sensitive data, pushes reduce the risk of data breaches and minimize the impact of a potential breach.
Automatic Expiration and Deletion
Pushes are designed to automatically expire after a duration or number of views, ensuring that sensitive data is not retained for longer than necessary. Once a push has expired, the payload is deleted entirely, leaving no trace of the sensitive data.
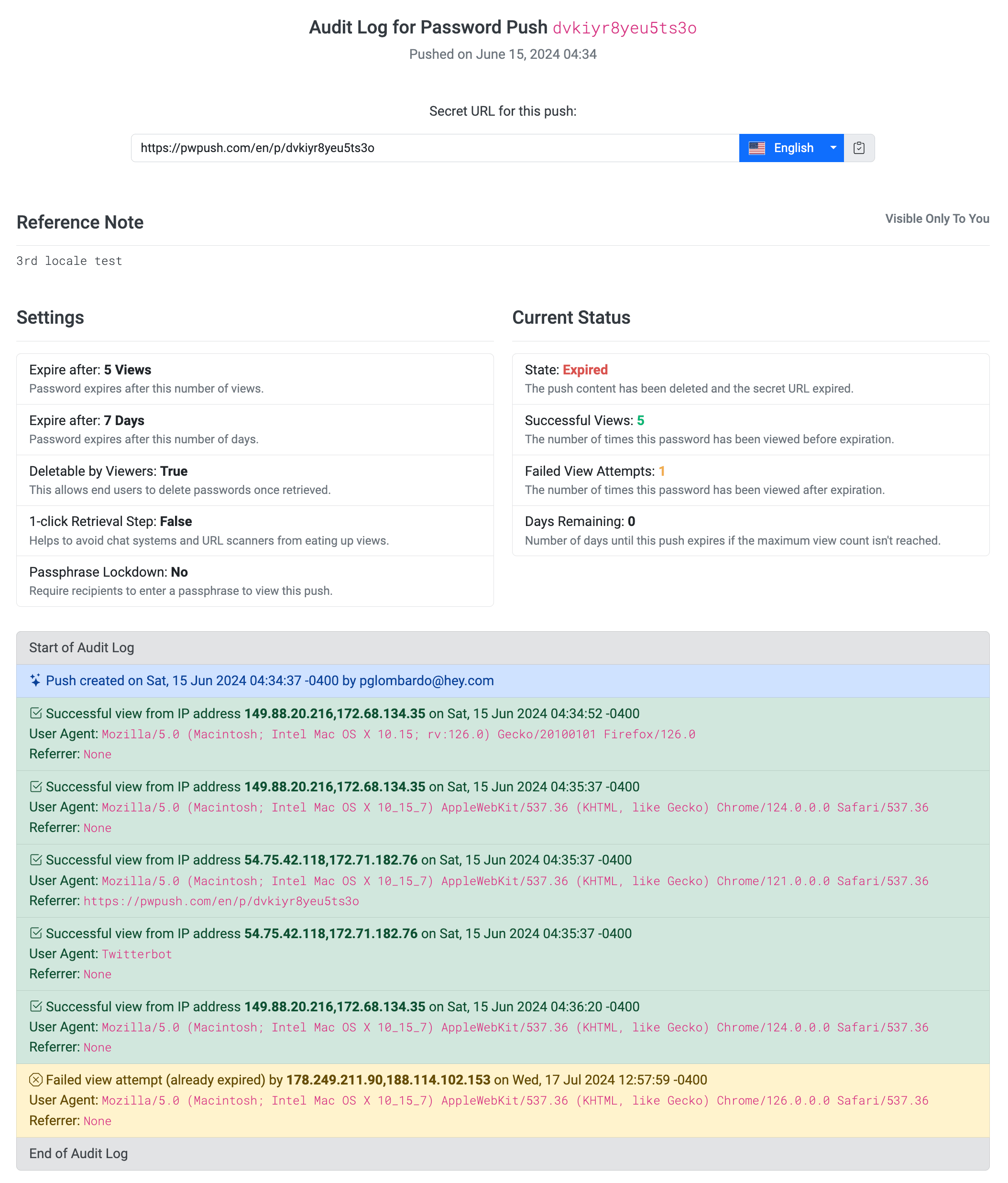
Comprehensive Life Cycle Tracking
The entire lifecycle of creation, access, retrieval, and deletion is tracked and logged providing a clear audit trail of all activities related to the push. This includes:
- Timestamps of creation, successful & failed access, expiration and deletion
- IP addresses, browser signatures and device information of users accessing the push
- Details of the push, including the type of data transmitted, expiration & deletion status
- Confirmation of deletion, ensuring that sensitive data is completely removed from the system
What do End Users See?
When an end user access the secret URL to a push, they will see a simple, unbranded delivery page that provides only the contents of the push. This page is designed to lower user confusion and provide a seamless experience for the end user.
Note: Premium & Pro subscribers get a fully branded delivery page. See here for more details.
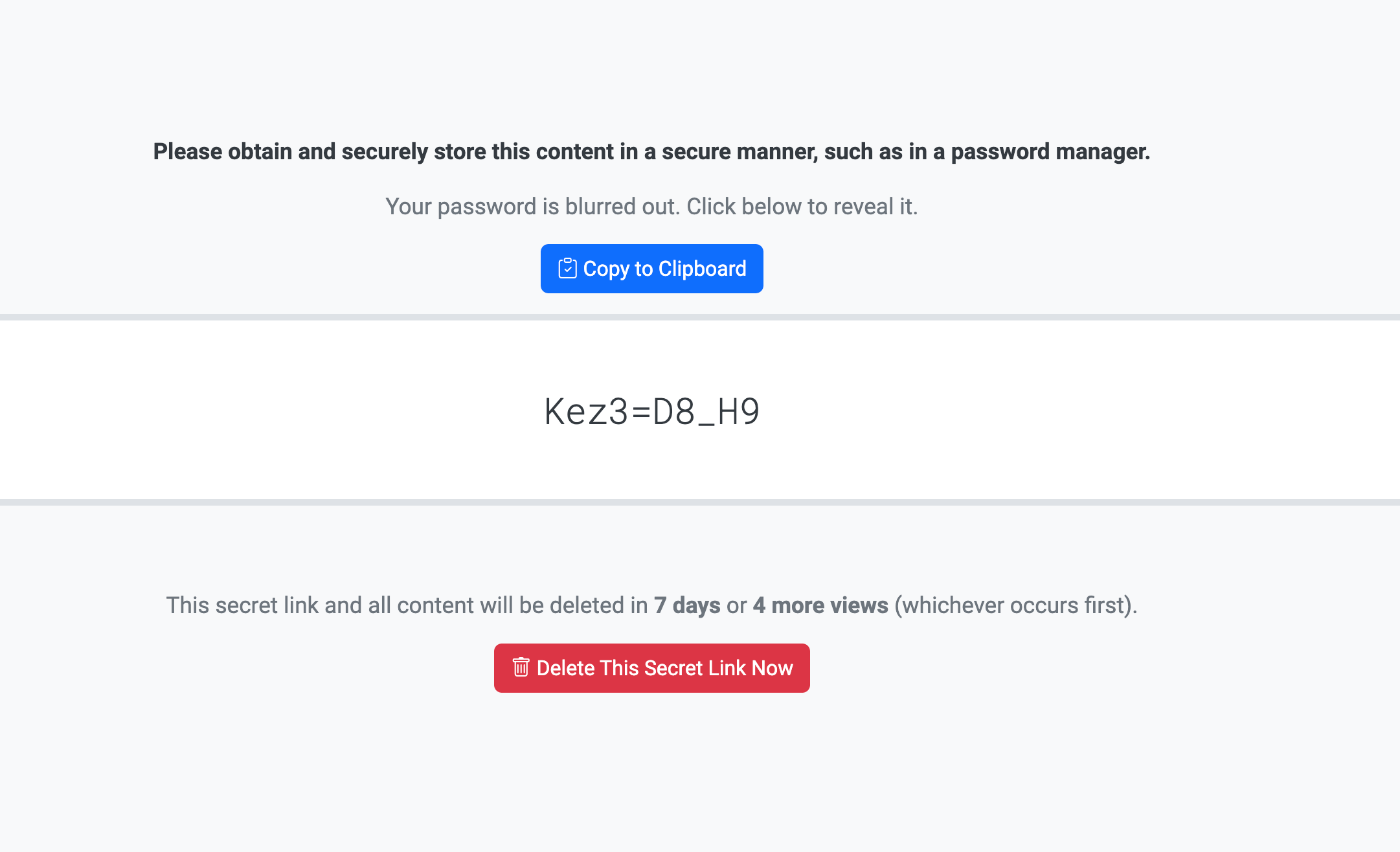
Push with Text
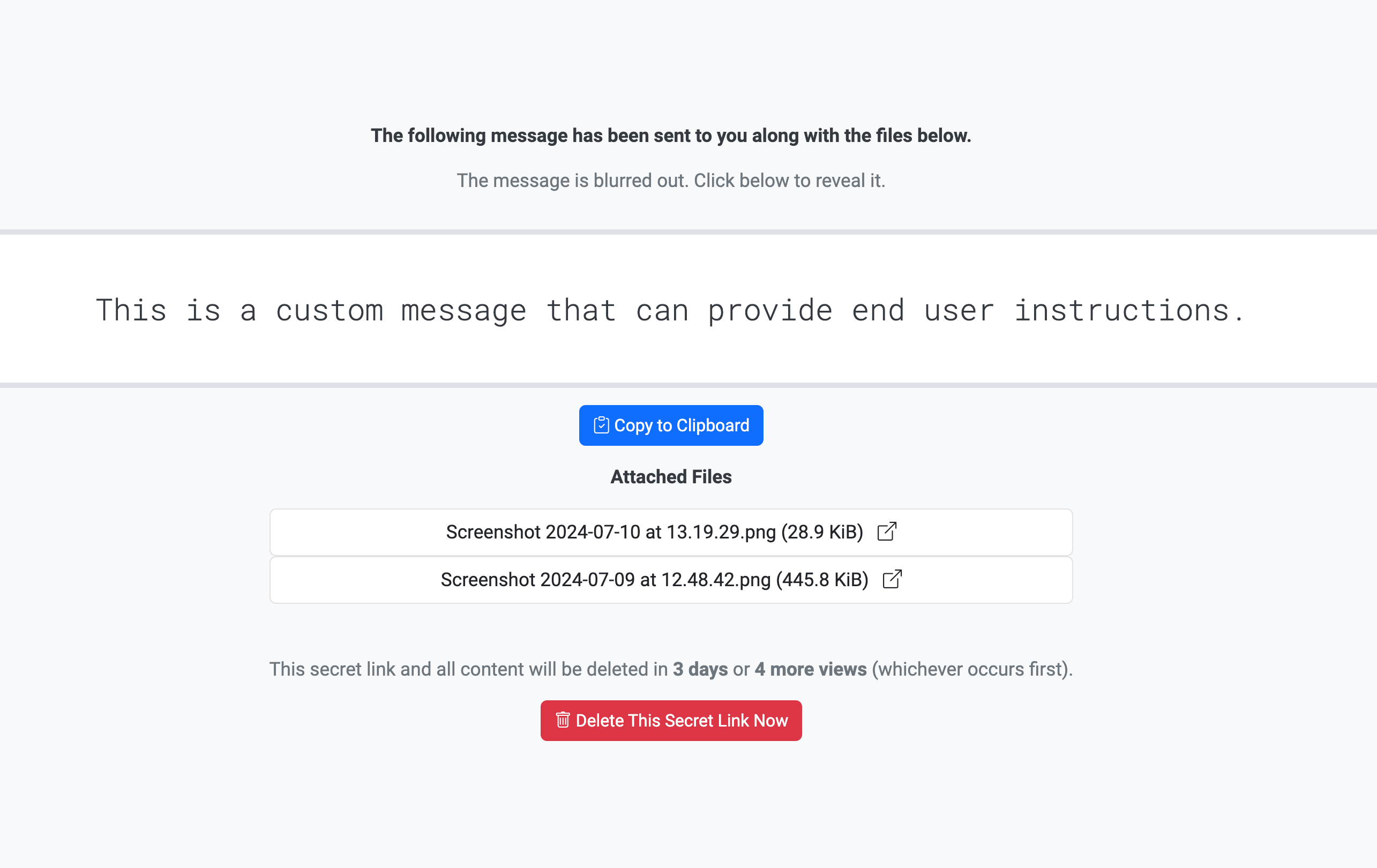
Push with Files
Expired Push

Pro Edition: Custom Domains
Custom domains allow you to fully white-label Password Pusher under your own company domain. When enabled, the entire application is available at the domain you specify — providing a seamless, branded experience for your users.
For example, with a custom domain configured, your Password Pusher instance becomes accessible at:
https://pwp.mycompany.org
All generated secret URLs will use your custom domain as well:
https://pwp.mycompany.org/p/secret-token
This means your users interact exclusively with your branded domain, reinforcing trust and maintaining a consistent company identity throughout the entire password sharing workflow.
Best Practices for Using Pushes
- Use Shorter Expiration Windows: The less time that sensitive information access is possible, reduces the risk of exposure. Limiting the duration and number of views that push provides increased security.
- Use Compartmentalization: Do not send passwords along with usernames or where they go to. Instead, use separate channels for transmitting passwords and other sensitive information.
- Monitor Push Access & Expiration: Make sure your users retrieve the information sent to them and that the push is expired appropriately and as quickly as possible.
- Use Passphrase Lockdown: Use the passphrase lockdown feature to require users to enter a preshared secret to access the contents of the push. This adds an additional layer of security and ensures that only authorized users can access the sensitive data. Both failed and successful passphrase attempts are tracked in the Push Audit Log.
Summary
Pushes provide a secure and efficient way to transmit sensitive data to end users. By encrypting and securely transmitting sensitive data, pushes reduce the risk of unauthorized access or exposure, improve user experience, and help organizations comply with regulatory requirements.
