Frequently Asked Questions
General
General
What is Password Pusher?
Password Pusher is a tool used for sending and receiving sensitive information securely.
With Password Pusher, you can create a unique, one-time URLs (a “push” or “request”) that self-delete after a specified duration or number of views.
Key features include:
- Automatic self-deletion upon expiration
- Detailed audit logs that track the entire lifecycle of your data
- Optional pre-shared passphrases for additional security
- Complete rebranding with your company identity
- Full featured JSON API for automation
New in 2025: You can now create one-time secure upload links to retrieve sensitive data from your customers, colleagues and clients.
What editions of Password Pusher are available?
Password Pusher offers multiple editions to meet different organizational needs:
| Edition | Description | Location |
|---|---|---|
| Premium | Complete security solution with file sharing and branding | pwpush.com |
| Pro | Team collaboration with custom domains and security policies | pwpush.com |
| Self-Hosted Pro | Enterprise-grade solution for private deployment | Self-hosted |
| OSS | Open source edition. Try it out here | Self-hosted |
Note: For a detailed comparison of features across all editions, please visit our Features Matrix.
What features are included in the Premium edition?
The Premium edition includes all features from the open source version plus:
- Secure File Sharing
- Share files up to 4GB
- Automatic expiration and deletion
- Branding Control
- Custom logos and images
- Personalized text and messaging
- White-label appearance
- Enhanced Security
- Advanced audit logging
- Detailed access tracking
- Optional pre-shared passphrases
For a comprehensive overview with screenshots, please visit our this blog post or review the detailed feature matrix.
What features are included in the Pro edition?
The Pro edition includes all features from the Premium version plus additional capabilities designed for teams and organizations:
- Team Collaboration
- Invite team members
- Shared dashboard and audit logs
- Team-wide security policies
- Custom Domain & Branding
- Run entirely under your own domain
- Complete white-label appearance
- Custom logos and messaging
- Team-specific branding
- Advanced Security Controls
- Team-wide 2FA management
- Custom security policies
- Priority support
For a comprehensive overview with screenshots, please visit our this blog post or review the detailed feature matrix.
What features are included in the Self-Hosted Pro edition?
Self-Hosted Pro includes all Hosted Pro features plus deployment on your own infrastructure: custom SSO (Google, Microsoft Entra ID, Okta, and more), flexible storage (local, S3, Azure Blob, etc.), and optional PostgreSQL for Enterprise. See the Pro Self-Hosted overview and Self-Hosted Pricing for details.
Trust & Security
What is the purpose of Password Pusher?
Password Pusher is a secure alternative to emailing or sending passwords via SMS, WhatsApp, or other messaging platforms. Emailing passwords is inherently insecure and poses significant risks, including:
- Passwords can be easily intercepted by malicious entities
- Emails can be hacked or compromised, leaving passwords vulnerable
- Passwords remain in perpetuity in email archives, even after they’re no longer needed
- Stolen or compromised email accounts can be used to retrieve and reuse passwords
Similarly, sending passwords via SMS, WhatsApp, Slack or other messaging platforms can also put your sensitive information at risk, as the data can be stored indefinitely and outside of your control.
Password Pusher solves these problems by providing a secure, temporary, and controlled way to share passwords. When you post a password to Password Pusher, we generate a unique URL that only you know, and the password expires after a set number of views or a predetermined time period. Once expired, the password is permanently deleted, ensuring your sensitive information remains secure.
Trust is a concern. Why should I trust and use Password Pusher?
Password Pusher exists as a better alternative to emailing passwords. It avoids having passwords exist in email & messaging archives in perpetuity. It does not exist as a end-all security solution.
Password Pusher started as an open source project at the end of 2011. It has been maintained & updated by myself (Peter Giacomo Lombardo) and a handful of excellent contributors for all of that time. In 2024, the premium version was introduced to accelerate development and to help fund the project. All premium features end up in the open source version eventually.
By having such a long history and being open source, Password Pusher has been reviewed by many eyes. It has been used by and audited many organizations and individuals over the years.
Push and request payloads are deleted entirely on expiration and the audit log is maintained indefinitely. The less data Password Pusher holds, the better.
If you still have concerns regarding trust, safety and security, feel free to review the code, post any questions that you may have and consider running it internally at your organization instead.
As for trust in me, all I can offer is my long history building this project (since 2011) and my public reputation on Github, LinkedIn, X and my blog.
Feel free to contact me anytime with any questions you may have!
How safe is it to post passwords using a tool like Password Pusher?
In the current day, where password generators are often used to produce high-entropy passwords, brute-forcing or performing a dictionary attack is extremely challenging. Thus discovering a strong password alone has very little value to attackers.
Without knowing the corresponding username and system it belongs to, a password is essentially useless. It’s only when two or more of these components - the password, username and system - are discovered together that they become valuable to attackers.
It’s for these reasons that sending a strong password alone with a tool like Password Pusher poses limited risk.
Then security is also improved if you use good security policies at your organization such as requiring two-factor authentication and periodic password resets.
Common best practices are to use multiple pushes, pre-shared passphrases and communicate over multiple channels (often referred to as segmentation or compartmentalization).
To even further increase security, Password Pusher also:
- encrypts sensitive data in the database
- has view and duration expiration limits
- deletes all sensitive data upon push expiration
- offers the use of optional pre-shared passphrases to further limit access
- maintains full audit logs that that reveal who interacted (and how) with the created push
- offers preemptive push deletion by you or optionally your end-user
- can be self-hosted internally at your organization
- is open source, has a +13 year history and the code been reviewed and audited many times over.
See also: What are the potential security risks of running my own version internally?
What is Apnotic?
Apnotic is the company created to manage Password Pusher (and to accept credit cards).
Premium Version
Password Pusher has always been open source. Why is there now a premium version?
Password Pusher has been very fortunate in it’s popularity and growth over the years. I’ve enjoyed every moment of building it and working with the community to make it better.
After 13 years, the project has hit a point where there are now more feature requests and ongoing maintenance than I can handle doing this only nights and weekends (which is a great problem for an OSS project to have honestly). On top of that, monthly hosting costs have also increased to a point where it’s starting to hurt a bit.
I introduced the premium version to help fund the project and to accelerate development. The super-set of features in the premium versions are meant to be a value-add for organizations that need more than the open-source version provides.
As Password Pusher is built out, premium features will periodically be moved to the open-source version.
Will the premium features be added to the open source version?
Absolutely - the premium version allows me to spend more time on the project. The final destination for all work is to be in the open source version of the project eventually.
Other features will go directly to the open source version.
What are the differences between the open source and premium version?
See the features page for a full list of differences between the open source and premium versions.
File uploads used to be free on pwpush.com. Why are they now a premium feature?
I really tried to keep file based pushes free but because of some abuse, risk and growing hosting costs. I didn’t have much choice.
If you are an individual or student and really can’t afford the subscription, message me and I will see what I can do. At a minimum, a credit card will be required even though it won’t be charged.
Note: File uploads are always available in the self-hosted version Password Pusher. This limitation is for unsubscribed pwpush.com accounts only.
Are there limits on the size of file uploads?
There are no hard limits on file upload size. Files up to 4GB have been successfully tested.
If you need to upload files larger than 4GB, feel free to contact us to discuss your requirements, and we’ll work to accommodate your needs.
Pro Version
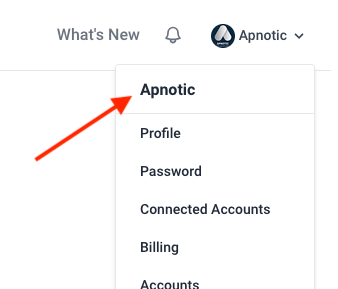
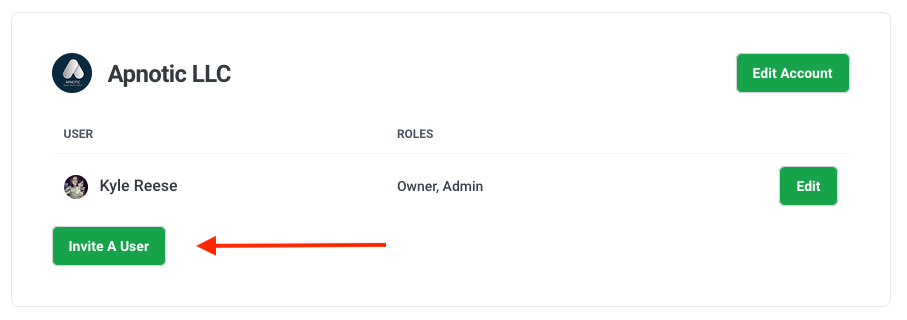
How can I invite users to my account?
You can invite users by selecting the top right dropdown menu and selecting your account. From there you should see an “Invite a User” button.
How do I add a custom domain for my account?
If you have a Pro subscription, you can configure your account with a custom domain under the Account Edit page.
See also: Rebranding with a custom domain
How do I hide some pushes and requests from certain invited users?
When you invite colleagues to your shared account, all users share a single dashboard, allowing for collaborative work. However, if you’d like to keep certain pushes and requests private or visible to only specific users, you can create a separate account.
Create a Separate Account
Your single login allows you to create and manage multiple “Accounts” (organizations, companies, or departments). Each account operates independently with its own dashboard, users, and subscriptions.
Example Use Case:
If you want your executive team to have a private space, you can create a new account called “Acme Executive Team” and create a new subscription for it. Only invited users for this account will have access to its pushes and requests.
Invite Users to Multiple Accounts
If needed, users can be invited to multiple accounts. For example, executives can be members of both “Acme Support Team” and “Acme Executive Team,” giving them access to both dashboards.
For More Information
Refer to the previous section for details on creating and subscribing to multiple accounts.
Subscriptions
Do you offer any discounts or free accounts?
We are pleased to offer the following:
Educational Discounts
Educational institutions receive a 15% discount. If your school, college, or university is interested, please contact us to apply this discount.
Charity Accounts
Charities are warmly welcomed! While we don’t have an official program, if you’re a charity, feel free to reach out, and we’ll do our best to accommodate your needs.
For-Profit Companies
If you’re part of a for-profit organization, your support through a subscription helps us continue to provide and build the open source project. We greatly appreciate your contribution!
If you have any questions or would like to discuss further, please don’t hesitate to reach out.
Billing
How do I add my company VAT ID or TAX ID to my invoice?
If you need to add your company’s VAT ID or TAX ID for tax compliance or to avoid being charged tax (for qualifying countries), follow these steps:
- Go to
/billingin your account - Click “Update payment method” - this will take you to the Stripe billing portal
- In the “Billing Information” section, click “Update Information”
- Add your Tax ID in the appropriate field
- Click “Save” to complete the update
Once you’ve updated your billing information in the Stripe portal, your VAT ID or TAX ID will be included on all future invoices.
Note: This change will apply to all future invoices. Previous invoices cannot be modified.
Reverse Charge Mechanism: For qualifying countries (such as EU member states), tax will not be charged when a valid VAT ID is provided, as the reverse charge mechanism applies.
Accounts
What is an Account on pwpush.com?
- Definition: An account on pwpush.com functions like a “team”, “department”, or “organization”.
- Features: Each account includes:
- Members: A dedicated set of users.
- Customized Branding: Tailored to reflect your team or organization’s identity.
- Security Policy: Specific security settings for your group.
How are Accounts Used?
- Corporate Use: Many users set up separate accounts for different teams within a corporation, for example:
- One account for the executive team.
- Another for the IT department.
- Another for the support team.
- Multiple Companies: Users with affiliations to multiple companies might create distinct accounts for each.
Account and Login Relationship
- One Login, Multiple Accounts: With a single login, you can create, manage, and be invited to multiple accounts.
TL;DR: Logins and Accounts have a one-to-many relationship. One login can manage multiple accounts.
Account and Subscription Relationship
- One Subscription, One Account: A subscription on pwpush.com is connected to a single account. The subscription will apply to the active account at the time of subscription.
TL;DR: A subscription on pwpush.com applies to a single account.
See also:
How do I switch between accounts?
After logging into pwpush.com, you can switch accounts using the account switcher found in the account menu:
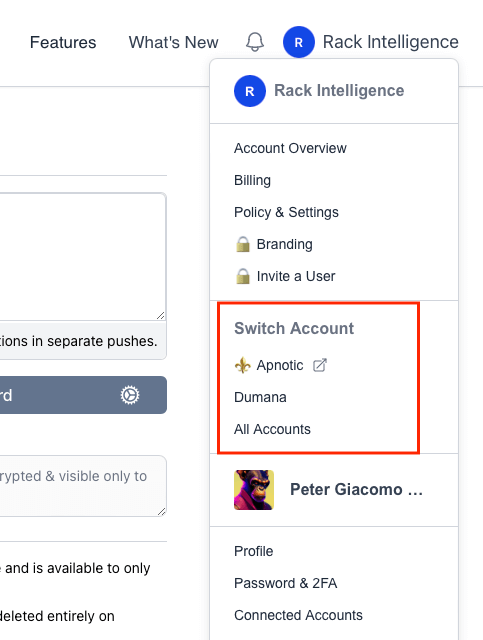
- To switch accounts: Simply click on one of the listed accounts to make it your active account.
- For Pro Accounts with Custom Domains: If you select an account with a custom domain, you’ll be securely redirected to that account’s custom domain.
Note: Ensure you’re logged in to see the account switcher.
How can I make my Pro account the default account when I log in?
If your account has a custom domain, log in directly at that custom domain instead of going to pwpush.com.
After a successful log in, that Pro account will be the active account.
Logins
Why am I seeing “We already have an account with this email…” when using Single Sign-On (SSO)?
We already have an account with this email. Login with your previous account before connecting this one.
This message appears when an account already exists with that email address but hasn’t been linked to SSO yet.
To resolve:
- Log in using your existing username and password
- Go to Sign-in Accounts under your user menu
- Click Sign in with Google (or your SSO provider) to link the accounts
After linking, you can use SSO for future logins.
Tools, Integrations & Applications
Are there other ways I can access Password Pusher outside of a browser?
With the Password Pusher JSON API, there are a number of applications and command line utilities (CLI) that interface with pwpush.com or your self-hosted instance. Push passwords from the CLI, Slack, Alfred App and more.
See the JSON API documentation page for more information.
Can I automate my password distribution?
Yes. The Password Pusher JSON API allows for the automation of password pushing. This can be done with a variety of programming languages, applications and tools.
See the JSON API documentation page for more information.
How many requests can I send to Password Pusher?
There are no limits currently and I have no intention of adding any. To minimally assure site stability, Password Pusher is configured with a rate limiter by default. This can be disabled in the self-hosted version.
Running Your Own Private Instance / Self-Hosted
Can I try the open source version before setting it up myself?
Yes! You can explore the latest version of the open source edition at https://oss.pwpush.com.
This live instance exists for the community. It lets you try out the features and functionality firsthand before deploying it on your own.
Can I run my own version for my organization internally?
Yes, for the open source version, we provide Docker containers and installation instructions for a wide variety of platforms and clouds.
For the premium feature set, Self-Hosted Pro is available — see Pro Self-Hosted and Self-Hosted Pricing.
See the installation documentation for more information.
Can I apply a custom logo or change the design?
The Premium and Pro plans on pwpush.com allow you to utilize fully branded and customized pushes. For the Pro version, you can invite colleagues to collaborate and even use a custom domain.
In both of those plans, you can also customize text, appearance and even hide features entirely from your team.
See here for a walk-through of all of the branding options in the Premium & Pro versions.
The open source edition of Password Pusher also supports complete re-branding “out of the box” allowing you to add a custom logo, images, text and even change the application theme.
See the Rebranding documentation for more information.
Are there any licensing restrictions for me, my company or my organization?
The source code of the open source version is released under the Apache 2.0 License and that pretty much defines any and all limitations. There are quite a few re-branded and redesigned clone sites across the internet and hosted internally I welcome them all.
pwpush.com hosts a premium version of Password Pusher with a super-set of features beyond the open source project. pwpush.com is free to use but offers subscriptions for the premium and pro features such as teams, invites, custom domains etc…
Self-Hosted Pro is available under a commercial license. See Pro Self-Hosted and Self-Hosted Pricing.
Why would I want to run my own private instance of Password Pusher?
Some organizations are bound by security policies that prohibit the use of public services for sensitive information such as passwords. There are even organizations that require all tools to be on private intranets without access to the outside world.
Running your own private instance of Password Pusher allows you to control the environment and the data. It also allows you to add custom features and integrations that are specific to your organization.
It’s for these reasons that we provide the ability (and encourage) users and organizations to self-host private instances when needed.
What are the potential security risks of running my own version internally?
Running a private instance of Password Pusher for your company or organization gives you the peace of mind that you know exactly what code is running. You can configure and run it as you like.
On the other hand, if your instance gets hacked and the encryption broken, malicious entities now have a targeted dictionary of passwords to brute force accounts in your organization. (this would be limited to pushes which haven’t expired yet)
In this respect, the public instance at pwpush.com may be superior in that it contains only passwords without identifying information mixed among users from around the globe.
One other consideration would be the maintenance of the instance. You need to keep it updated, secure and backed up.
You should carefully weigh the pros and cons and decide which route is best for you and your organization. We happily support both strategies.
Pushes
The secret URL I sent was already expired. What happened?
Some systems such as email, firewalls and chat systems often have link scanners that can eat up views. This is usually done for corporate security or to simply generate a “preview” for applications.
To prevent this, use the 1-click retrieval step option when pushing passwords. This requires the users to click through a preliminary page to protect views from such scanners.
As an additional preventative measure, when logged in, an audit log is provided for every push created. This audit log reveals by who and when the push was viewed.
A push I sent expired, but it contained important information. Can you retrieve it?
Unfortunately, no. Once a push expires, all sensitive information associated with it is permanently deleted and cannot be recovered. Additionally, Password Pusher has a strict policy to ensure user privacy, which means no team member can view or access user pushes at any time.
Audit Logs
In audit logs, why do I sometimes see multiple IP addresses for a single view?
Sometimes in the audit log, you might see multiple IP addresses listed for a single view (e.g., 1.2.3.4, 5.6.7.8). This is normal and happens when the viewer is accessing Password Pusher through various security or network systems. For example:
- Corporate networks often route traffic through security gateways
- VPNs and proxy servers act as intermediaries
- Cloud security services that filter web traffic
The first IP address is usually the original viewer, while subsequent ones are the various systems their HTTP request passed through.
Why is the referral sometimes blank in Password Pusher audit logs?
The referrer may not always be available for a variety of reasons. This is a result of the way web browsers and security policies are implemented.
Here are some of the reasons why the referrer may be blank:
Browsers Not Reporting Referrer:
Sometimes, the referrer information is not sent by the user’s web browser. This can happen for several reasons:
-
Privacy Settings: Many modern browsers have privacy features or settings that prevent the sending of referrer information to protect user privacy. For example, browsers might send only the origin, stripping out more detailed URL information when navigating across different domains.
-
Security Policies: Certain websites or applications implement policies like Referrer-Policy: no-referrer or Referrer-Policy: origin-when-cross-origin, which control how much referrer information is shared with external sites. This is especially common for security reasons, to prevent leakage of sensitive information about the source of the request.
Referrer Stripping:
Even when referrer information is sent, it might not be fully transmitted:
- Cross-Origin Requests: When a user clicks a link from one domain to another, browsers often send only the origin (domain name) rather than the full URL to enhance security and privacy. This means if a user accessed Password Pusher from another site, only the domain might be logged, or in some cases, nothing at all if the policy is particularly strict.
Direct Access
Sometimes, users access Password Pusher directly by typing the URL, using a bookmark, or through direct links shared outside of web navigation contexts (like in emails or messaging apps):
- No Referrer Source: In these cases, there’s no preceding web page to refer from, hence no referrer information is available to log. This is logged as a blank or “direct access” entry in the audit logs.
What is this unrecognized entry in the audit log?
If you notice an unexpected or unrecognized log in your push’s audit log, this is often due to automated scanning systems.
Here’s what commonly causes these additional views:
Link Scanners
Many systems automatically scan URLs for security purposes:
- Email security systems
- Corporate firewalls
- Anti-virus software
- Chat applications (like WhatsApp, Slack, Teams)
Tip: Want to see it yourself? Share a push URL (without the 1-click retrieval step) through WhatsApp, you’ll see an immediate audit log entry with “WhatsApp Bot” as the User Agent.
In most cases, the above scanners can be defended against by using the “1-click retrieval step” when creating pushes.
Browser Extensions: Some browser extensions pre-scan URLs for security or preview generation.
Corporate Security Systems: Many organizations use security systems that pre-scan all URLs that their employees access.
If you still don’t recognize the log and find it suspicious, you may want to expire the push immediately, change credentials if needed and attempt to send another over another channel (email instead of chat or slack instead of email).
Notes:
- The most effective way to prevent scanner views is to enable the “1-click retrieval step” when creating pushes
- Most legitimate scanning systems will identify themselves in the referrer field (like “WhatsApp Bot”)
- Some scanners may appear without a referrer, especially corporate security systems
- A missing referrer alone doesn’t necessarily indicate malicious activity
Tip: If the User Agent (browser information) between two logs are the same, it most likely came from the same computer directly. But then again, these HTTP headers can be spoofed so take that with a grain of salt.
JSON API
Why do I get “Invalid request parameters” or “Bad Request” when creating a push?
When creating a push, all values must be properly URL encoded. This is especially important when your payload contains special characters.
For example, if your payload contains the % symbol, it must be URL encoded as %25. Similarly, commas should be encoded as %2C.
| Original Text | URL Encoded |
|---|---|
Hi%Hello,Hola |
Hi%25Hello%2CHola |
This encoding is necessary because certain characters have special meanings in HTTP and must be properly escaped to be transmitted correctly.
Example:
curl -X POST \
--data "password[payload]=Hi%25Hello%2CHola" \
https://pwpush.com/p.json
Other
Can I use Password Pusher in my talk, video, presentation or conference?
Absolutely. We have media resources and a full explanation of features available in Windows Powerpoint and Mac Keynote formats.
If you have any questions or need any help, feel free to contact me anytime.
See the Presentations page for more information.
Can you add a specific feature for my organization?
Very likely as I’ve done so for many other organizations in the past.
I love to hear all ideas and feedback as it feeds the list of “what to add next”.
If you have any such requests, please let me know via one of the channels on the support page.
……………..
You made it to the bottom. Thanks for your time and attention. I hope I made everything clear.
If there is anything I can ever help with - feel free to contact me anytime.
